4 Healthy Habits to Avoid the Newest Crypto Scam
 |
| By Marija Matic |
Last week, I let you know that for crypto’s latest scam, the call is coming from inside the house.
GhostCalls are growing in popularity. This type of attack relies on clever social engineering to trick you into giving hackers access to your devices.
How? By hijacking your contact lists to make themselves look like someone you already trust.
Then, they use your information, likeness and even voice in some cases to do the same to others in your circle.
I suggest you read up on GhostCalls now if you haven’t yet.
Because today, I want to dive into how you can keep yourself safe … and what to do if you find yourself the target of a GhostCall.
Healthy Paranoia Is the Key to Prevention
For those who haven't been hit by a GhostCall attack, here's how to never become a statistic:
1. Never download files sent to you to “fix” video calls.
If a video call isn't working, there are a few steps you can take yourself to try and fix things. Use the web version instead of the app, switch platforms or reboot your device.
If all fails, you may even reschedule. Better yet, send your contact your own Zoom or Google Meet link instead.
No matter what, though, do not open the link sent to you through the chat.
Because ultimately, there is no legitimate technical reason someone would need to send you a file to fix Zoom.
This is generally enough to avoid a GhostCall scam. But I have a few other steps you can take, too.
2. Verify through different channels.
There’s a reason “verify, don’t trust” is still a deeply held crypto value.
If someone you know reaches out at random to schedule a call, ping them on a different platform to confirm.
If messaged on Telegram, follow up on WhatsApp. The real person won't mind switching platforms to talk. A hacker will.
3. Question convenience.
Sending links of professional scheduling tools and video calls is normal, so receiving them isn’t an immediate red flag. But they're also easy to fake, and the combination makes them an easy entry point for hackers.
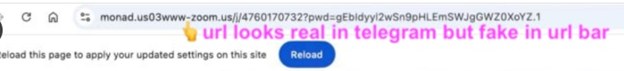
Take five seconds to verify the domain in the URL actually belongs to the service before you click.
For example, the URL below looks real in Telegram. But pasting it into an address bar reveals the full link … and the extra noise reveals the truth.
4. Trust the uncanny valley.
If something feels slightly off — if the person on the video looks weird, if the conversation flow is strange, if you feel even a whisper of doubt — hang up.
Your instincts exist for a reason.
If You've Been Compromised: Act Immediately
No matter how well you protect yourself, how vigilant you are, hackers can still find a way around your defenses.
If that happens, if you clicked that link and ran that "update," here's what you would need to do:
1. Disconnect immediately
- Turn off WiFi on the compromised computer.
- Power down the computer completely.
- Do not use it.
2. Secure your Telegram (Phone only)
- Open Telegram on your phone (not the compromised computer)
- Go to Settings → Devices → "Terminate all other sessions."
- Change your password.
- Enable two-factor authentication (you may want to do this now as a preventive measure).
- If you can't access Telegram, warn your network through other platforms that your profile has been hijacked.
3. Move your crypto using a clean device
- Using your phone or a different clean computer, create new wallets with new seed phrases.
- Transfer all crypto from exchanges and wallets to this new wallet.
- Change passwords on all exchange accounts.
4. Change ALL your critical passwords
This includes …
- Email accounts
- Password managers
- Cloud storage
And be sure to enable two or more verification methods everywhere.
5. Clean your computer before using it again.
- If your computer has been compromised, you’ll need to do a complete factory reset with hard drive reformatting.
- Reinstall your operating system from official sources.
- Do not restore from backups, as these may now contain malware.
The Broader Pattern: Adaptation is the Game
GhostCalls represent an evolution in social engineering.
And that’s the most unsettling aspect of this scam. Not the technical sophistication, but the betrayal of digital trust itself.
We've built an entire professional ecosystem on platforms like Telegram, Zoom and Google Meet. We've accepted that blue checkmarks and verified badges mean something.
We've trained ourselves to trust the interfaces and protocols of remote work.
And now, that system is being weaponized to rob us.
It’s clear to see why: This approach is faster, more scalable and harder to defend against because it hijacks real relationships rather than fabricating fake ones.
The criminals behind these operations are adapting faster than most people's security practices.
This particular campaign has been active since at least mid-2024, and it's only getting more sophisticated.
The latest evolution is particularly unsettling: North Korean attackers are now showing up at conferences in person.
These aren’t opportunists sitting in their moms’ basements. They’re highly skilled individuals who have studied what works and refined their techniques.
And now, they’re proactively making genuine face-to-face connections … then executing the video call scam weeks later. They're willing to buy plane tickets and conference passes to establish legitimacy.
When someone you actually shook hands with reaches out for a follow-up call, your guard drops completely.
And that's exactly what they're counting on.
Rather than run and hide, I hope you use the preventative measures above to help you stay safe and active on-chain and off.
The Uncomfortable Truth
There's no going back to a pre-digital world. And there's no perfect security that doesn't paralyze functionality.
What we can do is develop a healthier relationship with trust in digital spaces. One that balances necessary professional openness with appropriate skepticism.
Think of it as digital street smarts.
You don't refuse to walk outside because pickpockets exist. But you do keep your hand on your wallet in crowded places.
You shouldn’t refuse all video calls because hackers exist. But you should verify unusual requests.
And most importantly, never download files from people trying to "fix" technical issues remotely.
Best,
Marija Matić

