The GhostCall Comes from Inside the House with Crypto’s Latest Scam
 |
| By Marija Matic |
When I first wrote about pig-butchering scams, I focused on their slow burn nature …
The weeks of relationship building with carefully constructed personas, the gradual erosion of skepticism until victims willingly handed over their life savings.
It is manipulation at its finest. A con that relies on patience and human psychology.
But this latest crypto scam I'm about to describe is different.
It's faster, more technical and arguably more terrifying. That’s because it doesn't just steal your money — it steals your identity and turns you into a weapon used against people you know.
The Setup: Familiar Faces, Familiar Platforms
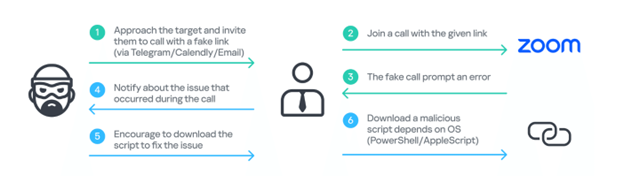
A GhostCall scam starts innocently enough.
Someone from your professional network reaches out via messaging platforms such as LinkedIn or Telegram. They won’t be a close contact, just someone you met at a conference, a VC you've exchanged messages with or a contact you chat with about crypto.
The conversation history is right there in your chat. You remember them. Of course you do.
And then their latest message comes in.
"Hey, how are you doing? It's been a while. Would you have some time this week or next week to connect?"
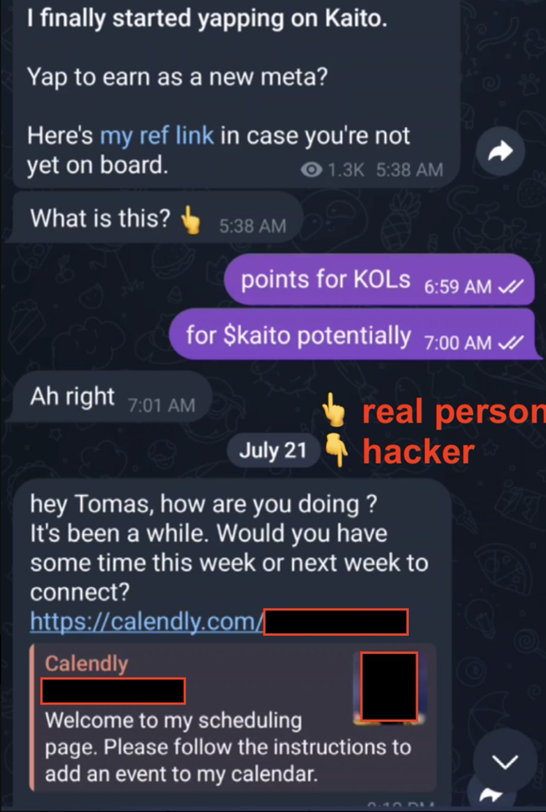
A Calendly link follows.
Everything looks normal. Professional. Exactly what you'd expect from a legitimate business contact trying to schedule a meeting.
You pick a time slot. A Zoom link arrives. You click it.
And that's when everything changes.
The Technical Sleight of Hand
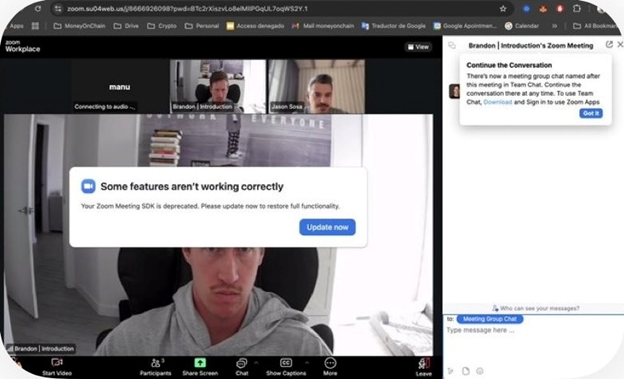
The video call that appears on your screen isn't actually live.
What you're seeing is a pre-recorded video of previous victims or footage pulled from public sources like podcasts and conference recordings edited together. Or, if the scammer is AI savvy, you may even see a convincing deepfake.
Then, you’ll see their mouth move, but no sound will come. Or in some cases, the sound quality will be off enough that you can’t hear them. The person might look slightly confused or annoyed.
But since you trust the contact, your brain fills in the gaps. Video calls glitch all the time, right?
Meanwhile, back on Telegram, your contact pings you with messages that feel eerily authentic:
"What's up, there’s no sound?" "Oh, Zoom is acting up?" "Yeah, don't worry." "I've faced this issue before too."
They're helpful. Understanding. They tell you it's just a technical issue that your Zoom needs updating. They even send you a screenshot showing exactly what to do.
They are, in the truest sense of the word, helpful.
Except they're not your contact. Your contact's Telegram account was compromised days or weeks ago. The person messaging you is a North Korean threat actor.
And they're watching your every move in real time.
The Malware: Hidden in Plain Sight
The "update" they send you is typically labeled something like "Zoom Update SDK.scpt."
But instead of a Zoom patch, it installs a sophisticated data exfiltration tool when you run it.
The virus systematically harvests everything:
- Cryptocurrency wallets on your computer
- Passwords stored in your password managers and browsers
- Your Telegram session authentication credentials (this is how they take over your messenger account)
- Anything stored in Notes or similar apps
It's thorough.
The Aftermath: From Victim to Vector
Here's where the scam transcends simple theft and enters truly dangerous territory.
Once they have your Telegram credentials, the hackers don't just read your messages.
They become you.
Just as they used your contact as a Trojan horse into your data, they’ll use your data the same way.
Making every person you care about in your contacts a target.
After all, the hackers now have a video recording of you to use in a GhostCall.
And while this social engineering attack propagates through your network like a virus, the malware is quietly exfiltrating every crypto asset you control, from your centralized exchange accounts to your self-custody wallets.
Your passwords get changed to lock you out, and suddenly you're watching your entire digital life disappear in real time.
The Scale: $300 Million and Counting
According to security researchers tracking these campaigns, North Korean threat actors affiliated with groups like BlueNoroff have stolen over $300 million using variations of this technique.
They are also famous for attacking casinos, ATMs and banks, including Bangladesh Central Bank.
The sophistication is important.
It means this isn't some lone hacker in a basement. This is an organized operation with clear objectives and refined methodology.
The targeting for this particular scam is deliberate. Cryptocurrency investors, DeFi protocol team members, blockchain developers and VCs in the space top the list of prime targets.
Essentially, anyone with access to significant digital assets or networked to other high-value targets.
Why Smart People Fall for This
You might be reading this and thinking, "I would never fall for something like this."
But there’s no such thing as too smart to be tricked. Because scams like these don’t rely on its targets to be dumb, just human.
Consider the psychology at play …
Social proof: The message comes from the account of someone you know, with complete conversation history. The scammer’s message comes through in the same chat you used legitimately before.
In the victim’s eyes, they’re not dealing with random strangers, so their guard isn’t up.
Technical plausibility: Video calls do have issues. Video conferencing platforms do need updates.
The scenario used to gain access to your data isn't outlandish. It's a normal part of working remotely in 2025.
Helpful manipulation: The scammers are patient, understanding and helpful. They alleviate your concerns before you fully form them.
In short, they've studied what makes people trusting. And they execute that playbook flawlessly.
Time pressure without urgency: They're not rushing you, but they are moving the conversation forward smoothly, preventing the natural pause where you might stop and question what's happening.
Really smart people — including developers who should know better, security-conscious crypto investors, experienced professionals — have fallen for this.
Because intelligence isn't the protective factor you think it is when facing social engineering this refined.
So, how can you protect yourself?
Definitely start with the basics. These are good habits that can keep you safe no matter what type of scam is popular at the moment. Things like …
- Keep your passwords away from online password managers and in more secure storage.
- Use hardware crypto wallets.
- Verify who you’re chatting with online or message them through another platform.
- Take a moment to check any link you’re sent.
As for the more advanced steps you can take — specifically those to help you spot and respond to a GhostCall scam — can get involved.
So, I plan to dive deep into them next Monday.
In the meantime, you can read up on other popular scams here and how to respond to them here.
Best,
Marija Matić