Build Your Own AI-Resistant Anti-Fraud System
 |
| By Jurica Dujmovic |
The fraud economics have flipped.
And while most investors haven't noticed yet, the numbers tell a striking story.
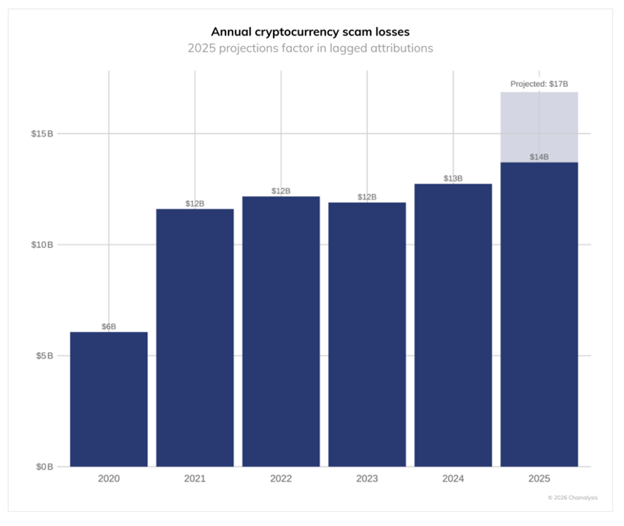
In 2025, scammers stole roughly $17 billion from crypto users through fraud and scams, according to Chainalysis data released in January 2026. That number dwarfs what was lost to protocol exploits and smart contract hacks.
The gap is widening. And the reason is AI.
The Fraud Flip No One Talks About
TRM Labs quantified the situation in late January: While general illicit trading volume increased by 143% last year, AI-enabled scam activity rose 500% over the same time, according to its 2026 crypto crime report.
(Though it is interesting to note that illicit volume as a percent of total crypto trading volume has decreased year-over-year.)
Related Story: The GhostCall Comes from Inside the House with Crypto’s Latest Scam
Why is AI fraud accelerating at a greater rate? Because it reduces the cost of operation across three key attack vectors:
-
Impersonation became trivial. Creating a convincing fake identity used to require significant effort. Now, an LLM can generate a coherent backstory, unique writing style and technical knowledge base in seconds.
Add voice cloning, and you can sound exactly like a protocol founder on a Telegram call.
-
Deepfakes erased verification shortcuts. "Just jump on a video call to confirm," used to be reasonable advice. Not anymore.
Google’s Threat Intelligence Group (Mandiant) documented a North Korea-linked operation that targets crypto firms in February 2026 using AI-generated deepfakes and sophisticated social engineering.
The attackers were able to impersonate legitimate contacts and deploy malware through “ClickFix” infection vectors disguised as troubleshooting help.
- Scale became frictionless. Running parallel scam operations across time zones and languages used to require teams. Now one operator can manage dozens of marks simultaneously with AI handling translation, context switching and persona consistency.
AI’s Latest Attack Hack: Address Poisoning at Scale
While deepfakes get headlines, a simpler but equally effective technique is scaling just as fast.
It’s called address poisoning. And it exploits a very human behavioral pattern: copying wallet addresses from recent transaction history instead of verified sources.
A recent peer-reviewed security paper presented at USENIX Security documented this attack at massive scale. It showed millions of wallets targeted and tens of millions in realized losses from poisoned-address transactions.
Attackers monitor on-chain activity to identify active wallets. Then, they send tiny transactions from addresses that look nearly identical to ones the victim actually uses.
This ensures the poisoned address appears in the victim’s transaction history.
When the victim copies what they think is their own address or a frequent trading partner's address, they accidentally copy the attacker's, instead.
Millions of wallets have been targeted. Realized losses run into tens of millions. The attack works because it exploits muscle memory and interface design.
This is the pattern across AI-enabled fraud: Tiny UX exploits outperform sophisticated code exploits because humans are the weaker link.
Why This Matters Right Now
While hackers are living in an AI-powered future, crypto investors are still playing defense against 2021's threats.
They worry about smart contract audits and protocol vulnerabilities. But that’s not where you’re likely to face a real threat.
To be clear, you should still do your due diligence and review a platform or project’s audits and weaknesses. But if you’re not protecting yourself against the greater threat, you leave a lot of your crypto exposed.
And we’re seeing that the most vulnerable access point isn’t on chain.
It’s YOU.
And scammers are now using AI to weaponize your trust with shocking success. You now effectively run leverage on your security posture without realizing it.
Every Telegram DM, every token approval, every address you copy from transaction history carries amplified risk in an AI-enabled fraud environment.
A Crypto Investor Anti-Fraud Operating System
Generic security advice doesn't work here. You need concrete, immediately implementable changes to how you operate on-chain to stay safe.
Here are six big steps you can take to increase your personal security …
1. Stop trusting identity in crypto communication.
Social media is still how most crypto projects communicate new developments or solicit community engagement.
Now, though, you have to treat every Telegram and Discord DM as hostile by default.
Impersonation is the core mechanism of modern fraud. If someone reaches out claiming to be from a protocol, exchange, or investment group, it’s imperative that you verify their identity through multiple independent channels.
That means a known domain email address, a verified social media account and, ideally, a reference from someone you know personally.
2. Video calls no longer provide verification.
Deepfakes are good enough to fool careful observers in real-time conversations. The only reliable verification is out-of-band confirmation through channels you initiate and have verified, not channels someone else suggests.
3. Eliminate address copy-paste errors.
This one may feel counterintuitive since we are all used to the ways computers have streamlined many of our administrative tasks. But when transferring crypto, use an address book or whitelist system for every wallet you interact with regularly.
Never copy addresses from recent transaction history.
For significant transfers, you may even consider implementing a test-amount protocol. That is, send a tiny amount first and confirm receipt on a separate device before you complete the full transfer.
This two-step approach catches both poisoning attacks and simple copy-paste errors.
4. Reduce your hot wallet blast radius.
Keep only actively trading amounts in hot wallets, also known as software wallets. These are your browser extensions — MetaMask, Phantom, etc.
Everything else belongs in cold storage, also known as hardware wallets. These are USB-like devices that can be completely disconnected from the internet. And that keeps your long-term holds safe from unnecessary exposure.
This isn't exciting advice, but it's the highest ROI security measure available.
It may also be useful to keep different wallets for different strategies — long-term holds, trades, DeFi permissions, airdrops, etc. This way, contamination from a compromised approval or malicious contract doesn't cascade across your entire portfolio.
5. Maintain regular wallet health checks.
This means you should treat approvals as recurring liabilities. Token approvals persist until explicitly revoked. Many users approve protocols during high-activity periods and forget about them.
Those approvals remain active attack surfaces.
Which makes regular audits and revoking unnecessary approvals a necessity for proper wallet health.
You can use tools like Revoke.cash or Etherscan's approval checker to see what protocols have access to your wallet.
Better yet, use wallets that simulate transactions before signing and flag suspicious approval requests.
6. Assume all “support” is a scam vector.
The Mandiant case study shows the exact pattern: Fake support offers that deliver malware disguised as troubleshooting tools. While no one wants to be so pessimistic, the data proves the best way to stay safe is to remain skeptical.
This means you should never install software, run command strings, or import “recovery phrases” suggested by anyone claiming to provide support.
Real protocol support happens through official channels with verifiable identities. They’ll never DM you first, never ask for seed phrases and never send you software to install.
(And neither will Weiss Ratings!)
The Strategic Implication
This isn't temporary. AI capabilities will only improve from here.
Voice cloning will get better. Deepfakes will become even harder to detect. LLMs will handle longer, more complex social engineering campaigns.
The fraud attack surface will continue to expand faster than the exploit attack surface because AI scales human manipulation better than it scales code auditing.
Your approach to on-chain security needs to reflect that reality.
The investors who survive this cycle will be those who treated behavioral OPSEC as seriously as they treated protocol selection.
Every other security measure will soon prove secondary to not trusting the wrong person at the wrong time.
The data is clear. The mechanisms are documented.
The only question is whether you'll upgrade your security practices before AI-enabled fraud finds you.
Best,
Jurica Dujmovic
P.S. One thing that’s not a scam? Adding dividend-paying stocks to your financial strategy.
Weiss Ratings founder Dr. Martin Weiss just revealed his new Infinite Income Strategy that’s looking to outperform the market 16-to-1 with dividends!
He explains everything in his recent Infinite Income Summit. We’re taking it offline tonight, so be sure to watch this recording before then!