Over $40 Million in Crypto Stolen from U.S. Gov. Wallet
 |
| By Mark Gough |
Wallet security is one of the most important elements of crypto investing.
If any bad actor gets access to your wallet, that’s it. They can now control your crypto holdings.
That’s why it’s so important never to give out your passphrase or keys.
And why my colleagues Marija Matić and Beth Canova have given you great tips on how to keep your wallet safe over the years.
But it seems the U.S. government is learning about wallet safety the hard way.
Millions in Seized Crypto, Gone
The beauty of crypto is that it is transparent.
All transactions are recorded on the public blockchain. So anyone can review them to make sure everything is above board.
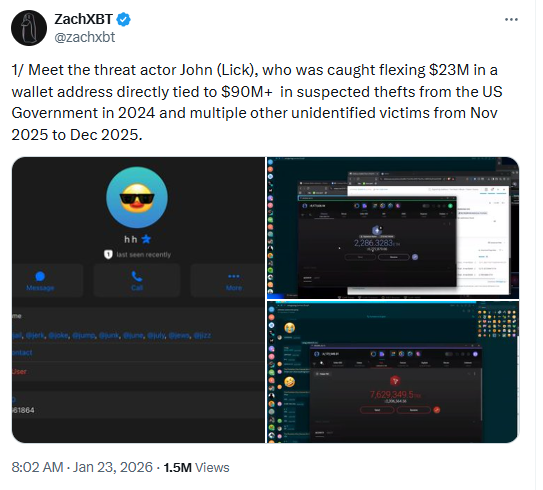
And one on-chain investigator — ZachXBT, who has built a reputation for tracing illicit crypto flows and exposing wallet-level misconduct — recently found something big.
They were able to link a pseudonymous user, “John Daghita,” to more than $90 million in suspected thefts from a wallet controlled by the U.S. government.
That wallet held crypto seized from illicit activities like hacks from the past two years.
Those funds were supposed contribute to the U.S. Strategic Bitcoin Reserve.
Crucially, ZachXBT’s preliminary investigation points to ongoing access, rather than a single exploit, operational error or accidental transfer.
Even more concerning was a small but revealing transaction: 0.6767 ETH, worth roughly $1,900, sent directly to ZachXBT’s publicly known wallet address.
While modest in dollar terms, the transfer implied something far more serious: Whoever controlled the wallet had full signing authority.
That means they could move funds freely, without multi-party approval or automated safeguards intervening.
For wallets assumed to be under government control, that should not be possible.
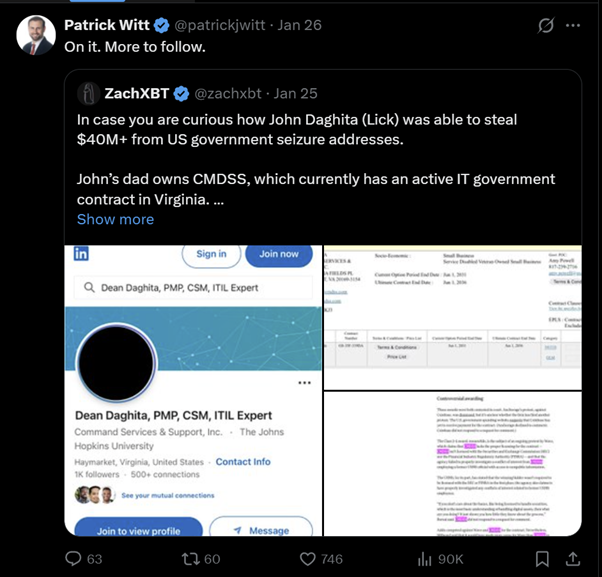
Witt Acknowledges the Claims
Shortly after the allegations became public on X, Patrick Witt — Executive Director of the President's Council of Advisors for Digital Assets — responded directly:
The response was brief but notable. As head of the White House Crypto Council, Witt sits at the center of U.S. crypto policy, custody oversight and the administration’s broader digital asset strategy.
His public acknowledgment signaled that the claims were being taken seriously at a senior policy level.
U.S. Marshals Confirm Investigation
Following Witt’s response, the U.S. Marshals Service confirmed it had opened an investigation into potential unauthorized access to government-owned cryptocurrency wallets.
Early reporting suggests investigators are examining whether a contractor or a contractor’s family member may have gained access to the wallets in question.
If accurate, this would point to an internal control failure rather than an external cyberattack.
The Marshal’s Service has long been responsible for managing seized assets, including cryptocurrency obtained through criminal forfeiture.
The case now raises questions about how those custody systems were structured and whether access controls were adequate for assets that can be transferred instantly and irreversibly.
Why the Timing Matters
The allegations surfaced as the Trump administration pushes to advance the CLARITY Act — the long-awaited legislation intended to bring comprehensive market structure and regulatory clarity to U.S. crypto markets.
For policymakers who argue that crypto is ready for full regulatory integration, this custody integrity matters.
Regulatory clarity assumes that assets — especially those held or administered by the state — are governed by robust operational controls, clear accountability and strict access management.
This hack could shake public confidence for all of that.
A Familiar Problem in a New Context
Crypto custody failures are not new.
What makes this case notable is that we assume government wallets were held to a higher operational standard than private-sector custodians.
In practice, crypto custody still hinges on a small number of fundamentals:
- Who controls the private keys
- How many approvals are required to move funds
- Whether access is segmented, audited and continuously monitored
Once a transaction is signed and broadcast, it cannot be reversed. If assets were improperly moved, recovery may be difficult or impossible unless funds can be intercepted at centralized intermediaries.
And that’s assuming they have not already been laundered or swapped.
In short, the government faces all the same risks you do when securing your crypto wallet and verifying transactions.
Now, the U.S. needs to prove it is savvy enough to stay secure on the blockchain.
What Comes Next
As the investigation continues, several questions remain unresolved:
- How was access obtained in the first place?
- Were multi-signature or hardware-based controls in place?
- Which assets were affected, and in what amounts?
- Have any funds been recovered?
The answers will matter not just in this case, but for how the U.S. approaches digital asset custody more broadly.
If Washington wants to pass the CLARITY Act and eventually build bipartisan agreement around a strategic Bitcoin reserve, custody failures like this will only make that task harder.
For now, federal investigators continue to assess the scope of the incident.
In the meantime, I hope you take this reminder to lock down your own wallet security. Here are two Weiss Crypto Daily updates that can help you get started:
Best,
Mark Gough